FICAM Governance
Identity, Credential, and Access Management Subcommittee
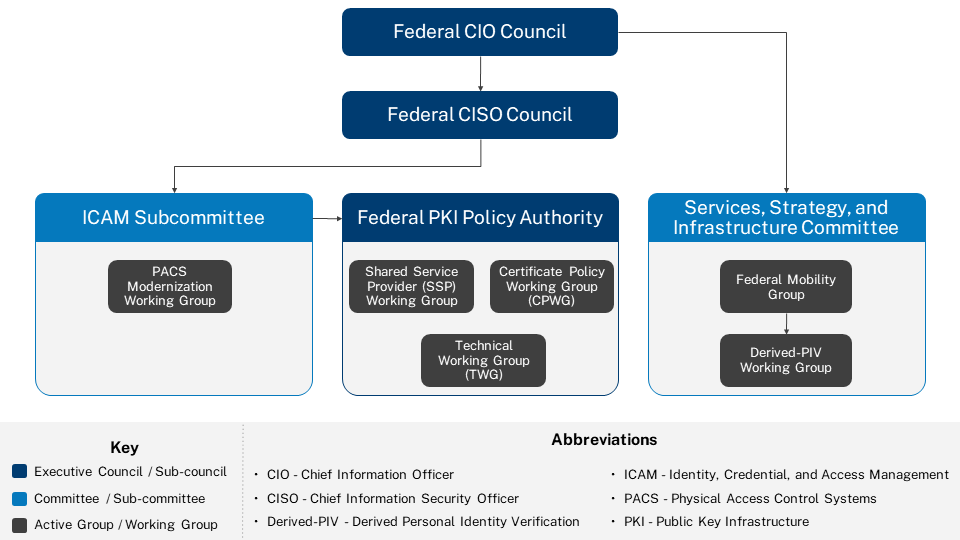
The Identity, Credential, and Access Management Subcommittee (ICAMSC) is the principal interagency forum for identity management, secure access, authentication, authorization, credentials, privileges, and access lifecycle management. It’s a sub-committee of the Federal CIO Council’s Federal Chief Information Security Officer (CISO) Council.
The ICAMSC is co-chaired by the GSA Office of Government-wide Policy and another volunteer agency (currently the Department of Justice). The ICAMSC aligns the identity management activities of the federal government and supports collaborative government-wide efforts to:
- Increase agency flexibility in addressing ICAM challenges;
- Coordinate interagency efforts to meet agency mission needs;
- Identify gaps in policies, procedures, standards, guidance, and services; and
- Align ICAM policies and compliance with other cybersecurity initiatives.
Activities
- Address Agency Challenges: Provides opportunities for agencies to troubleshoot issues and challenges associated with the planning, implementation, and operations of ICAM programs and solutions.
- Develop Policy Recommendations: Recommends new ICAM policies and updates existing ones.
- Provide Flexible Tools for ICAM Programs: Develops specific tools to assist agencies’ abilities to meet ICAM policy objectives and overcome ICAM implementation challenges.
- Facilitate Communications and Information Sharing: Acts as a vehicle for cross-government collaboration by sharing information, lessons learned, and best practices related to ICAM.
Membership and Meetings
Membership is open to federal agency employees with a .gov or .mil email address. Contractors are permitted to join on a case-by-case basis. See the ICAMSC Meeting Page on Max.gov for more information. Access to the page requires multifactor authentication using either Max Secure+ or a PIV/CAC.
ICAMSC Working Groups
The ICAMSC charters working groups based on a defined purpose and timeline. See the complete list of active and inactive working groups at the ICAMSC Max.gov page. Send an email to icam at gsa dot gov for more information or to join a working group.
| Working Group Name | Purpose | Activities | Membership Requirements | Meeting Schedule |
|---|---|---|---|---|
| Physical Access Control Systems Modernization (PACSMod) | Facilitate the implementation and use of the technology and processes related to modernizing electronic-PACS (ePACS) within the federal government (USG). | By September 30, 2021, develop a PACS Assessment Toolkit, a self-assessment that agencies can use to assess the FICAM compliance of PACS implementations. | Federal employees and designated contractors operating a PACS. | Monthly |
Other ICAM Working Groups
Other ICAM working groups may be charted under other committess or subcommittees of the Federal CIO Council.
| Working Group Name | Purpose | Activities | Membership Requirements | Meeting Schedule |
|---|---|---|---|---|
| Derived-PIV Working Group | Accelerate the implementation of mobile identity management across the federal government. | Document and share PKI and non-PKI use cases to increase the available technical and information resources. Provide a feedback look to inform policy and standard. | Federal employees and designated contractors | Monthy |
ICAM Community Listserv
The Federal ICAM Community Technical Listserv (ICAM-COMMUNITY-TECH List) aims to provide a communications platform to share and discuss technical issues impacting the federal ICAM community. Members hope to leverage the knowledge of ICAM aubject matter experts to identify, share, and hopefully resolve technical issues that exist in agencies and departments. This list is open to anyone with a .gov email.
Subscribe by contacting the list owner: ICAM-COMMUNITY-TECH-request at LISTSERV dot GSA dot GOV with subscribe in the subject line.
Federal Public Key Infrastructure Policy Authority
The Federal Public Key Infrastructure Policy Authority (FPKIPA) serves the interest of federal organizations as relying parties and promotes interoperability between federal and non-federal entities by:
- Setting policy governing the Federal Public Key Infrastructure (FPKI) Trust Infrastructure;
- Approving applicants for cross certification with the Federal Bridge Certification Authority (FBCA)
- Providing oversight to the Certified PKI Shared Service Provider (SSP) Program.
FPKIPA is co-chaired by the GSA Office of Government-wide Policy. The GSA Office of the Chief Information Officer (OCIO) is responsible for security authorizations and continuous monitoring for commercially-operated PKI shared service providers.
Activities
- Approve Policies and Practices – Approve Federal Bridge Certification Authority (FBCA) and Federal Common Policy Certification Authority Certificate Policies (CPs), including revisions; approve FPKI Trust Infrastructure Certification Practice Statements.
- Approve Entity Cross-Certification – Establish and administer criteria and methodology for cross-certification with the FBCA; approve cross-certifications and execute Memoranda of Agreement (MOAs); maintain the FPKI Certification Applicant Requirements and the Common Policy CPS Evaluation Matrix.
- Maintain Compliance – Ensure cross-certified entities are compatible with the FBCA CP (or the Federal Common Policy Certification Authority [FCPCA] CP for Federal Legacy CAs).
- Ensure Agreement with FPKI Management Authority – Oversee the FPKI Management Authority (FPKIMA) to issue and revoke cross-certificates, ensure adherence to the FPKI CPs, and provide documentation to be archived.
- Coordinate Interoperability Practices – Coordinate legal, policy, technical, and business practices and issues related to FPKI Trust Infrastructure.
Membership and Meetings
Each federal agency’s CIO appoints members and the group operates under the authority of the Federal CIO Council through the Information Security and Identity Management Committee (ISIMC) and the Identity, Credential, and Access Management Subcommittee (ICAMSC). See the FPKIPA Charter for information on membership requirements, voting rights, etc.
FPKIPA members meet in the morning on the second Tuesday of each month. Contact fpki at gsa dot gov to participate in the FPKIPA or its working groups.
Federal Public Key Infrastructure Management Authority
The Federal Public Key Infrastructure Management Authority (FPKIMA) enables government-wide trust by providing trust infrastructure services to federal agencies. The FPKI Policy Authority (FPKIPA) governs FPKIMA and the GSA Federal Acquisition Service manages it.
Activities
- Manage Digital Certificate Policies and Standards Ensure secure physical and logical access, document sharing, and communications across federal agencies and between external business partners.
- Operate the FPKI Trust Infrastructure, Operate two main certification authorities (CA):
- Federal Common Policy CA (FCPCA): It is the trust anchor for the federal government. Authorized CAs issue certificates for exclusive use by the federal government for federal employees and contractors to include the PKI certificates on the Personal Identity Verification (PIV) credential.
- Federal Bridge CA (FBCA): It is the PKI Bridge that enables interoperability between and among federally operated and business partner PKIs.
FPKIMA Newsletter
- FPKIMA Newsletter (Winter 2023) “NIST Identity Guideline Revisions”
- FPKIMA Newsletter (Fall 2022) “Post Quantum Updates”
- FPKIMA Newsletter (Winter 2022) “ALPACA”
- FPKIMA Newsletter (Summer 2021) “EO Improving Nation’s Cybersecurity”
- FPKIMA Newsletter (Spring 2021) “Federal Common Policy CA Update”
- FPKIMA Newsletter (Winter 2021) “FPKIMA COVID-19 Response”
- FPKIMA Newsletter (Fall 2019) “New Federal Identity Guidance”
- FPKIMA Newsletter (Spring 2019) “The Big Bridge Issue”
- FPKIMA Newsletter (Winter 2018) “GSA ACES Program Sunset Update”
If your agency is experiencing issues related to the FBCA or FCPCA, please contact fpki-help at gsa.gov
Federal Public Key Infrastructure Working Groups
The FPKIPA charters three ongoing working groups and as well as other short-term working groups and tiger teams.
If you meet the membership criteria and wish to join a working group, email fpki at gsa dot gov and include the text “Request to Join xx,” where “xx” is the name of the working group.
| Working Group Name | Purpose | Activities | Membership Requirements | Meeting Schedule |
|---|---|---|---|---|
| Certificate Policy (CPWG) | Advise on Federal Bridge and Common policies. | Facilitate proposed Certificate Policy changes, facilitate the FPKI cross-certification process, and address and resolve issues through policy analysis and modification. | Federal employees, designated contractors, and PKI providers involved in the FPKI. | As needed. |
| Shared Service Provider (SSPWG) | Advise the Shared Service Provider Program. | Identify policy changes that impact the Shared Services Providers Program and address and resolve issues through policy analysis and modification. | Only FPKI Shared Service Provider representatives. | As needed. |
| Technical (TWG) | Investigate and resolve complex FPKI technical issues. | Identify and scope technical FPKI issues, address security concerns and vulnerabilities, and identify technical improvements to enhance security and operational capabilities. | Federal employees, designated contractors, and PKI vendors. | As needed. |


